Guidance topics related to research data and security are arranged alphabetically from A-Z and described below. Each topic is linked to its page location and may also include links to corresponding policies, guidance and/or templates. If you are unable to find an answer to your question below, please contact Research Compliance, Integrity, and Security.
Best Practices for Protecting Research Data
Cloud Storage
Cybersecurity Maturity Model Classification (CMMC)
Data Destruction
Data Security/Data Management Plans
Data Sharing
Data Use/Data Transfer Agreements & MTAs
Document Version Control
Encryption
Microsoft 365: OneDrive/Sharepoint/Teams
Mobile Apps/Software
Research Data Complexities Impacting Risk Assessment
Research Records Best Practices
Sensitive, Restricted, or Confidential Data & Issues to Consider
Tele/Video Conferencing (Zoom/Microsoft Teams)
Travel & Data Security
Additional Resources
Best Practices for Protecting Research Data
The following are general best practices research personnel should keep in mind and follow in order to appropriately safeguard research data:
- Access only the data you are authorized or have appropriate need to access (just because you may have access, doesn’t mean you have a legitimate need to look at or share the information)
- Don’t request access unless you truly need it
- Remove access when it is no longer needed
- Work with the data responsibly
- Comply with all laws, policies, regulations, sponsor agreements/contracts when handling data
- Follow the University of Nebraska Research Data Security requirements
- Take extra care when traveling- be cognizant of the type of data you could have with you or access and where you are traveling in the world (if you have controlled, sensitive, restricted, or confidential information do not travel with it and be very careful about knowing if you can or should access it on your trip)
- Take extra care when working remotely (e.g. from home, or away from campus)
- Understand your use of personal devices (e.g. mobile phones), what data you are working with, and whether it should be accessed from a personal or mobile device
- Do not use personal accounts or equipment to collect, access, maintain, or share University research data
- Use cloud services responsibly- know whether information is controlled, sensitive, restricted, or confidential and if it can be uploaded to a cloud service such as UNL SharePoint/Restricted SharePoint or OneDrive.
- Store data in appropriate places
- Understand where specific types of data can be safely stored (physical server, cloud storage, flash drives, student computers etc.)
- Be particularly aware of working with data covered by HIPAA, FERPA, CUI, CDI, ITAR, or EU GDPR
- If you would like to use cloud storage/collaboration options, ensure you know how to use it securely and what data can and cannot be stored
- Properly manage or destroy information and devices
- Follow all data retention requirements, any approved protocols, and security rules
- Securely dispose of any physical media or records containing data
- Report
- Don’t wait to gather your own evidence or resolve it yourself, report immediately if you suspect or know of a data breach
- Do not continue to forward or include others that don’t need to know about a data breach concern. Redact information when needed in order to mitigate unauthorized sharing of information
All research personnel should review and utilize the following checklist in order to ensure data security practices are followed:
Cloud Storage
The use of cloud storage can be a very helpful and convenient way in which research teams access, generate or store research data. However, research personnel must be cognizant of what type of data they intend to place in a cloud environment and whether or not it is appropriate for the corresponding research data security level. One of the most important factors for researchers to remember, besides security of the data, is that, in most cases, the research data belongs to the University of Nebraska-Lincoln and not the researcher. It may be common practice to utilize cloud services for cost savings and ease of use; however special attention must be paid to potential security risks, confidentiality, export control restrictions, and data ownership issues.
Currently, the University’s sanctioned cloud-based storage is available via Microsoft One Drive and/or SharePoint/Restricted SharePoint. In general, Low or Medium Risk de-identified research data will usually not be problematic to store data in the cloud-based storage options, however, Medium and High Risk export controlled research data, may not be stored using these options. High Risk research data may not be stored in unrestricted OneDrive or SharePoint, unless the PI has received prior approval from NU ITS and the applicable research oversight body.
Due to data ownership and security oversight needs, research personnel are not allowed to store this information outside of UNL networks or systems, regardless of the data security level. However, if you are considering the storage of any data outside of UNL networks, research personnel must have approval to do so and the following questions, at minimum, will be required to be addressed by the University and applicable research oversight body:
- Does the agreement with the vendor/collaborator stipulate the University owns the data?
- How will the vendor/collaborator make the data available in the event of an incident, breach, or disaster?
- What security controls are in place to prevent the inadvertent or malicious disclosure of the data?
- What happens if a subpoena is issued?
- Does the vendor have Information Security/Cyber Liability insurance?
Collecting or storing research data using the internet results in additional complexity as one must consider the jurisdictional authority: is it the jurisdiction of the researcher, the location of the study participants, or the location where the data is stored? Data may be collected in one jurisdiction but then stored in another. Researchers need to be aware that there may be differing data security privacy policies. It is important that researchers consider the laws, including international laws and export control regulations, and if needed, have agreements in place to ensure compliance.
Additional Resources:
- UNL Export Control Compliance Program: CUI/CDI & Microsoft 365 US Government
Cybersecurity Maturity Model Classification (CMMC)
Cybersecurity Maturity Model Certification (CMMC) Guidance
The Cybersecurity Maturity Model Certification (CMMC) ensures that organizations handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) implement appropriate cybersecurity practices to safeguard sensitive data. Compliance is required for recipients of funding from the Department of Defense (DOD) and is increasingly relevant across federally sponsored research and partnerships.
Overview
CMMC integrates cybersecurity standards and best practices from multiple sources, including NIST SP 800-171 and NIST SP 800-172, into a unified framework. It establishes three certification levels, each representing increasing maturity and protection standards. Practices such as access control, incident response, audit & accountability, system & communications protections, risk management, and security assessments are all included as part of these standards and expectations.
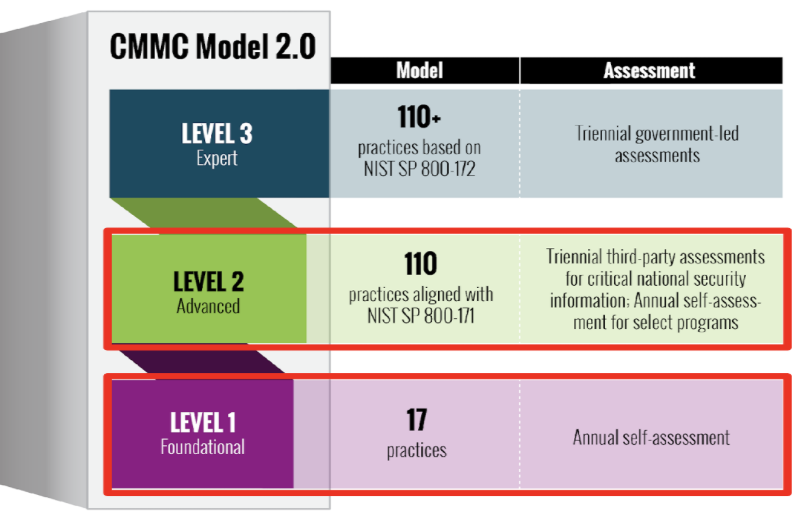
Timeline
- September 10th, 2025, CMMC Final Rule published in the Federal Register.
- November 10th, 2025, 60 days after publication, the CMMC Final Rule goes into effect. CMMC Level 1 Certification and some conditional Level 2 will be required. (CMMC Level 2 Conditional Certification requires the University of Nebraska submits and maintains a self-assessment of our cybersecurity practices via a SPRS score).
- Following this date, new DOD solicitations and contracts will start requiring some level of CMMC as a condition of contract award.
- Nov 10, 2026, most DOD contracts will require full CMMC Level 2 Certification. (Full CMMC Level 2 Certification requires the University of Nebraska to engage with an outside entity to evaluate and certify our cybersecurity practices).
NU ITS and the UNL Office of Research & Innovation have been collaborating regularly to ensure these requirements and the associated timelines can be met. UNL recently completed an updated CMMC Level 1 self-assessment. UNL’s Level 2 self-assessment is in process and will be completed soon. Ongoing work is planned to continue to meet the full CMMC requirements for Level 1 and Level 2 over the course of the next year. NU will engage with a certified 3rd party (C3PAO) for formal assessment and certification prior to November of 2026. Level 3 may or may not be achieved, depending on leadership decisions, prioritization, and budgeting.
What is a SPRS Score?
A SPRS score is a numerical rating in the Department of Defense’s (DoD) Supplier Performance Risk System (SPRS) that assesses a government contractor’s progress in implementing the NIST SP 800-171 security controls. It is used to determine a contractor’s cybersecurity risk and is a required part of contracts that involve controlled unclassified information (CUI). The score is calculated by subtracting points for each unimplemented NIST security control from a baseline score of 110. NU ITS and the Office of Research work together to submit and maintain this score.
What does this mean for research personnel?
- As of November 10th, 2025, solicitations and contracts will state the CMMC level required to submit a proposal and/or accept an award. When considering whether to submit a DOD proposal, research personnel must carefully review the solicitation information and understand what CMMC Level is required. While DOD will be checking the University of Nebraska’s SPRS score information to assess whether we are eligible to apply or accept an award, research personnel must also understand and be knowledgeable of the cybersecurity requirements for a particular project and whether practices will allow the work to be carried out.
- Sub awardees will also be required to comply with directed levels/cybersecurity requirements. Whether UNL is a prime awardee or a sub awardee, research personnel must be cognizant of what is being stipulated and working with Sponsored Programs and the RCIS Office to ensure requirements can be met, prior to work commencing.
Resources
- UNL Research Security Overview template: https://research.unl.edu/researchcompliance/research-data-security-templates-forms/
- UNL CUI and CDI Guidance: https://research.unl.edu/researchcompliance/activities-subject-to-export-controls/#CUI_CDI
- DoD CMMC Program: https://dodcio.defense.gov/CMMC/
- NIST SP 800-171 Rev. 3: https://csrc.nist.gov/publications
- Project Management Office (PMO) CMMC Resources: https://www.acq.osd.mil/cmmc/
Data Destruction
When a research project has ended or no longer has use for certain data, the PI may want to consider destroying the data.In general, the PI is responsible for the destruction of research data and the destruction must follow all applicable federal regulations, UNL policies on record retention and data disposal, sponsor requirements, research oversight body requirements, NU ITS requirements, and other applicable guidelines.
For research data destruction, secure disposal procedures should be utilized commensurate with the security level of that information and its related risk. (e.g., with increased risk associated with a data breach or loss of the data, the data media should be physically destroyed). If the data classification or sensitivity is unknown, at a minimum, the PI should consider the data classification as High Risk.
Devices or media containing private-restricted or highly restricted information (i.e. Medium or High Risk) must be physically destroyed or the information must be destroyed, deleted or overwritten using tools or techniques to make the original information non-retrievable. Overwriting should, at minimum, consist of a single pass with an industry standard and validated media sanitization tool supporting overwriting with all zeroes or all ones.
When destroying research data, the PI or research personnel should plan to retain documentation for audit purposes in order to record that the data was destroyed appropriately and in compliance with all regulations, agreements or policies. Destruction of research data documentation shall be retained by the unit.
For High Risk data that has been removed or destroyed, a sample form is available via the National Institutes of Standards and Technology.
For export controlled or controlled unclassified information or media, please contact the Export Control Office for assistance.
In addition, University of Nebraska Information Technology Services policies and information should also be referenced regarding the retention and destruction of data.
Data Security/Data Management Plans
Data security/data management plans (DMPs) are required as part of many research areas (IRB and Export Control being two areas frequently requiring these plans) and often times are required by specific federal sponsors. Typically, these plans are contained within their respective compliance applications and/or sponsor proposals/award. However, in many cases, additional oversight and separate security/management documents may be necessary in order to clearly detail how the data will be secured and managed throughout the life of the project.
DMPs must address not only how or where research data will be stored but also how it will be generated, accessed, transmitted, stored, and secured. When needed, and dependent on the security level of the data, NU ITS staff can assist you with research data security and storage, provide cost estimates when applicable, set up systems and more. Appropriate research data security and management can be costly, researchers must recognize the importance of planning for this process before a grant proposal or research protocol is submitted so any needed budget submissions can be included where possible.
The following are questions research personnel should think about when planning their research DMP needs:
- What data security level will be used?
Be sure and consult the Research Data and Security policy and guidance information regarding security level designations (Low, Medium, and High Risk). The appropriate level will need to be selected as part of many research oversight body processes.
- Who will be responsible for the data/machines/equipment?
- If Medium or High Risk data will be involved, data that cannot be stored via approved cloud computing, will need to be housed in an NU ITS designated area.
- Will any government owned equipment be provided? What is the value, and will it require tagging in the UNL system?
- Where will data be stored?
Regardless of how much data your research will generate you should have a storage system in mind that will meet the needs of the project and the security levels. While USB drives, hard drives, and disks are cheap and easy solutions they do not provide great security and can be easily lost or destroyed.
- If you are working with human subjects data:
- What physical and electronic security requirements will be in place for protecting the research data?
- Will individuals be identified during data collection or in the results?
- How long will they be identifiable?
- Will the data be coded, if so, will there be a list linking names and codes?
- Do you have any PHI information subject to HIPAA? Any FERPA information?
- If you are working with export-controlled data:
- What physical and electronic security requirements will be in place for protecting the research data?
- Are there any DFARS clauses that are applicable?
- Are there foreign national restrictions?
- Is Microsoft 365 US.gov required?
- What are the record retention requirements?
This will depend on the type of data involved and what regulatory or contractual requirements may be needed. - Who has access to the records/data?
PIs must know who has access to research data and whether or not any restrictions or confidentiality parameters are necessary. - Will data will be shared during or after the research?
- Are any data transfer/use agreements(DTUA/DUAs) or MOUs required?
- Are any data management plans required?
- Are any special requirements needed for transmitting data (e.g. encryption, 365.gov etc)?
*Please see the Data Sharing guidance below for additional information regarding data sharing.
- How will data be reported and are there restrictions on publications?
PIs must ensure data has been appropriately de-identified or, they have adhered to sponsor/contractual requirements for publication approvals.- Are there any data sharing requirements involved, at the end of the project?
- Does your funding source stipulate certain DMP requirements or format be addressed?
- Many sponsors and agencies provide clear templates and rules regarding the submission of DMPs. Please reference the information further below to access tools in this area.
The following provide additional resources for DMPs along with a couple of templates for use:
- UNL Data Security/Management Templates – IRB & Export Control (found on the Templates/Forms webpage)
- DMP Tool this website maintains a large listing of DMP resources and templates for different funding agencies. Research personnel should reference this site when a funding source requires certain DMP information be addressed.
- NU ITS Password Best Practices: https://its.unl.edu/bestpractices/password-management
- NU ITS International Travel Best Practices: https://its.unl.edu/bestpractices/international-travel
Data Sharing
The sharing of research data is a vital aspect of promoting transparency, public trust, and rigor within scientific fields. In some cases, a specific data sharing plan must be created in order to meet federal or other requirements. In other cases, data sharing may not be possible due to certain types of data having national security or military use concerns. The following are some areas research personnel must consider when planning their research projects:
Please Note: New data sharing policy and data sharing/management plan requirements for all NIH funded research studies is forthcoming and will be effective January 25, 2023. The NIH has created several new resources regarding these upcoming requirements. Visit the new NIH website on this topic here and watch NIH’s YouTube video about the new site here.
WHAT data will be shared?
- What types of data are to be collected in the study and shared?
- Will individual-level data or raw data be shared?
- Will the full data set be shared?
- What data quality control measures will be implemented?
- What data documentation will be shared?
- What commonly accepted data standards will be used?
WHO will have access to the data?
- Will the general public have access to some or all of the data?
- Will access to certain data be restricted to qualified researchers?
- If data access is restricted, what are the justifications/criteria for restricting access?
- Are publication restrictions stipulated by the sponsor or other federal requirements?
- What will researchers need to do to comply with any data access restrictions?
- What data sharing agreements will be necessary?
- Who will be operationally responsible for ensuring that no personally identifiable information is made available?
WHERE will the data to be shared and/or located?
- Will an existing data repository, or archive be used to store and disseminate the data?
- Will a new repository need to be developed, and if so, who/what will maintain the repository?
- Will the data be distributed directly by an investigator to those who request it)?
WHEN will the data be shared?
- The schedule for release of data:
- What data, if any, will be shared prior to publication?
- What data will be shared upon acceptance for publication?
- If using a repository, when will data be submitted to the repository?
- Will data from ongoing longitudinal studies be released in increments as data become available?
- How will data maintenance and access be ensured after the award ends?
- Will there be support for continued sharing of data?
HOW will researchers locate and access the data?
- What steps will be taken to help researchers know that the data sets exist?
- How will the data be accessed (web service, ftp, etc.)?
To share or not to share. The following table may help describe why data sharing is important or why data sharing may not always be feasible:
| Reasons to Share Data | Reasons NOT to Share Data |
| Demonstrate appropriate stewardship of taxpayer funds | National security concerns |
| Enable validation of research results | Publication restrictions |
| Honor contributions of human subjects research participants, where available | Informed consent did not adequately or appropriately notify human subjects research participants how data would be shared |
| Promote transparency, rigor, and reproducibility | Proprietary/Intellectual property sponsor restrictions |
| Make high-value data sets available | Restricted data sets, or the combination of data sets that allows for re-identification |
The following information, FAQs, and template are provided to further assist in addressing data sharing requirements:
- UNL Data Sharing & Publication Agreement Template (Available on the Templates/Forms webpage)
- Key Elements in Preparing a Data Sharing Plan
- NIH Data Sharing FAQs
- UNL Library Data Management: The UNL Library provides resources to assist with data management as well as operating a data repository
- UNL Data Repository: The UNL Data Repository was created to provide for the growing requirements by external funding agencies for data management and data sharing. This repository, designed to provide researchers with a secure site for storage of data collections that are no longer actively in use. Data will be preserved on UNL Libraries servers and backed up locally and remotely on a regular schedule. Upon acceptance, datasets will be provided with a unique identifier (DOI), and will be discoverable through the UNLDR and Libraries’ Encore search interface (following any embargo period, if applicable).
Data Use/Data Transfer Agreements & MTAs
DUAs/DTUAs and MTAs are contractual documents for the use of a portion of data, transfer of a portion of data or a complete set of data where the data is nonpublic or is subject to some restrictions. Universities must ensure that DUA/DTUA terms protect confidentiality, intellectual property, and security when necessary, but permit appropriate publication and sharing of research results in accordance with Federal, State and University regulations.
Research personnel are not authorized to complete these agreements. The Office of Sponsored Programs Awards Team is responsible for coordinating the transfer of data to or from another institution via a DUA, DTUA, or MTA. They will ask for information about the research, such as a project description, your funding, and compliance requirements (as applicable). They will consult with the IRB, NUtech, Export Control, IBC, and IACUC and any other applicable research oversight body, as needed for the agreement.
Agreements generally need to be in place for both incoming and outgoing data. The following are some points that you should ensure the OSP Awards Team is aware of when they are assisting you with requesting or receiving data:
- Does the data include “Personal Identifying Information” (PII), “Protected Health Information” (PHI/HIPAA), identifiable education records (FERPA), or other personal, private or financial information that may not be publicly shared?
- Is the data obtained from human subject research participants, even if de-identified?
- Do any members of the research team have financial interest(s) in the data provider/recipient?
- Does the data have specific security requirements, citizenship access restrictions or penalty for not complying with the contract or award?
- Does the incoming agreement stipulate that the data provider will own or control your research results, or may approve or restrict your publications?
- Does the agreement contain language that subjects the University to liability, such as insurance and indemnification terms, or statements that the agreement is governed by foreign law?
- Is the data subject to obligations to others (e.g., is restricted by a sponsored research agreement, or derived from other data)?
Departments and research personnel should be particularly careful when an investigator is leaving UNL. In many cases, if the person that is departing does not have another institution/university that they plan on moving to, it may be difficult to share data and ensure appropriate stewardship. Discussion and consideration with the OSP Awards Team along with the applicable research oversight area should occur prior to any decisions being made regarding the transfer of data under these circumstances. This same process should also be followed if any data disputes or litigation arises regarding the transfer or ownership of the data.
Additional resources:
Document Version Control
Version control is a process used to keep track of and communicate, in a standardized manner, different drafts of a document. This process is important as it provides an audit trail for the revision and update of a finalized version. In particular, this process can be most readily utilized by researchers to track different versions of research documents, agreements, or consent forms that may be used in order to ensure the most current, and approved, document is being used.
Research personnel are encouraged to implement the use of version numbers to track the most up-to-date document. While there are many ways to approach version control of documents, this is the standard operating procedure used by Research Compliance, Integrity, and Security. Please feel free to reference and use this SOP as needed.
UNL Guidance for Document Version Control:
Encryption
Encryption is the process of using algorithms or codes to transform electronic data to make it unreadable or inaccessible to unauthorized users.
Encryption should be implemented on storage devices (i.e. data “at rest”) and to network data (i.e. data “in motion”) in order to protect data when security requirements are necessary.
- Example of data at rest: an excel file of research data on the hard drive of a desktop or laptop.
- Example of data in motion: using a web browser to download research data from a remote server.
Encryption will not always be required when working with Low Risk research data. If you plan to store or work with Medium Risk research data, encryption may be needed; High Risk research data will always require encryption.
Remember, the best way for ensuring sensitive or confidential data is managed appropriately is to avoid handling it. This type of data should only be stored or accessed when it is deemed necessary for your research.
Examples REQUIRING encryption either at rest or in motion:
- Research data that includes Export Controlled, PII, or Protected Health Information AND
- Computing device is a mobile device OR
- Computing device is a personal system OR
- Storage device is removable (portable) OR
- Access to the storage device is not in a physically secure environment.
- Use of electronic research data that includes personal and/or Protected Health Information AND
- The information is being sent by:
- Email OR
- Webmail OR
- Web browser OR
- Traditional mail (US Post Office) OR
- Courier OR
- Instant Messenger OR
- Peer-To-Peer network OR
- Wireless (Wi-Fi, Cell phone, etc.) OR
- A backup of the information is created
The process of transmitting and storing data is often overlooked as a risk. Research personnel must plan prospectively regarding how to protect confidentiality and security. They should describe the methods to protect the data during collection and sharing both internally and externally to the University. It is advisable to utilize a secure transmission process even if the data is anonymous, coded, or non-sensitive information. If the research team develops a best practice on using a secure data transmission process, then it is less likely a data breach will occur. Email notifications are generally not secure, except in very limited circumstances, and should not be used to share or transmit research data as a normal practice. Text messages are stored by the telecommunications provider and therefore are not secure. Data should be encrypted when “in-transit,” and the University provides extensive guidance, software, and resources to assist researchers in this. Terms such as Secure Sockets Layer (SSL and HTTPS) or Secure File Transfer Protocol (SFTP) are indications that the data is being encrypted during transmission.
To learn more about encryption, please visit the NU ITS Best Practices webpage.
Microsoft 365: OneDrive/Sharepoint/Teams
With the 2021 UNL transition from Box storage to equivalent Microsoft options, the following brief summaries may be useful to research personnel becoming familiar with and utilizing these storage options:
- OneDrive: These are your personal university files, or you want to keep them private from others in your research group. You can decide if you would like to provide others access, person by person. In general, research personnel should be aware that OneDrive files will be deleted upon someone’s departure from UNL. Therefore, a plan for ensuring continued access to these files may need to be in place if others need access or if they contain university owned data.
- All files that you share, or that others share with you, can also be accessed in OneDrive.
- SharePoint/Teams: This is where your group can work, and everyone included as a member of the group has access to all files.Research personnel must be particularly aware of what is being shared and who in their group should/must have access when using Sharepoint and/or Teams. In general, information stored on a SharePoint site will remain available and owned/transferrable to others at UNL if a group member leaves the university.
- If you want to utilize a SharePoint site, you must contact ITS to request set up. When requesting this site be created, research personnel must pay close attention to whether the site will be private or if it could be accessible to those outside the group. This request form will ask what type of site is needed: SharePoint Request Form
- Restricted SharePoint: This is a restricted site that provides additional levels of security beyond normal SharePoint. If you need to utilize a Restricted SharePoint site, you must contact ITS to request set up:
- Restricted SharePoint Request Form – https://its-forms.nebraska.edu/210905244436855
- General: Some storage options and requirements are not free and are an additional cost. If you have questions about costs and/or specific storage needs such as Restricted SharePoint (equivalent of Restricted Box) or Microsoft 365.gov (for ITAR/specific export-controlled information), you can contact ITS, or use their storage request via the following: Storage Request Form
For further guidance, including FAQs, information on storage size limits, security, and privacy of these options, please reference the University of Nebraska ITS webpage. ITS also provides training information and guidance regarding One Drive and SharePoint here.
Mobile Apps/Software
Some researchers purchase mobile apps/software or build their own to interact with study participants or as a novel approach in research or intellectual property. It is important for research personnel to seek expert IT review and, if commercially available, purchase the app through the UNL Procurement Office so a legal and data security review is performed.
Specific to human subjects research, if participants are asked to download a free app/software or provided monies for the download, the researcher is still responsible for disclosing potential risks. It is possible that the app/software the participant downloaded will capture other data stored or linked to the phone/iPad etc on which it is installed (e.g., contact list, GPS information, access to other applications such as social media). The researcher is responsible for understanding known or potential risks and conveying them to the study participant, whether the app/software is commercially produced or developed in house.
Commercially available apps/software publish “terms of service” that detail how app data will be used by the vendor and/or shared with third-parties. It is the researcher’s responsibility to understand these terms, relay that information to participants or their applicable research oversight body (e.g. IRB/export control compliance program), and monitor said terms for updates.
Research Data Complexities Impacting Risk Assessment
Research data is an everyday part of the work completed at the University of Nebraska-Lincoln. Since it is common to create it, use it, and store it, the responsibilities and expectations associated with research data may be forgotten or overlooked. Some key points include:
- Research data involved in work at UNL is almost always property of the University of Nebraska (see EM41). The University has a commitment to following all applicable federal, state, and University regulations.
- The Principal Investigators (PIs) and other research personnel are stewards of research data, and expected to follow the policies and procedures of the University.
- Researchers are responsible for classifying the risk associated with their research data, but the applicable research oversight bodies (such as Animal Safety, Biosafety, Export Control, IRB, etc.) holds the final say on the assigned risk classification for research data. Risk classifications also have to match contractual and sponsor/award specific rules and regulations.
Why Does Risk Assessment Matter?
In practice, knowing the risk level of the data being stored allows us to apply the necessary digital or physical security measures needed. At a higher level, these measures protect against unintended access and cybercrime, safeguarding intellectual property, public safety, advanced technologies, national defense, etc.
All research data requires some level of security. Even when data is classified as low risk, we want to protect against data loss or manipulation by unauthorized users. UNL uses a variety of baseline security measures that apply to all digital data, and all faculty, staff, and students are expected to follow basic digital hygiene. The baseline measures are considered common good costs, but unique security needs can incur additional costs. In general, the higher the security needs, the more costly the data storage and computing solutions needed. Also, higher risk is typically paired with limitations on how data is accessed.
What Makes Research Data Complex?
There are two main reasons that research data is complex and may need to be treated differently than other data on our campus.
- As part of the research, data is often processed in a way that changes the associated risk. The most common example of this is through deidentification – where the information that would point to the source, location, time, or other sensitive information is removed or masked within the data.
- What is “risky” in data is going to depend on the project. In some projects, references to time, either when the data was collected or a specific event, is not at all of concern and does not change the risk assessment. However, in other projects, it can make it easier to identify the source of the data, which is something we need to protect against. Overall, this variability from project to project, and the groundbreaking work UNL researchers are doing result in a need to address many issues on a case-by-case basis.
Over the data life cycle, data may move through different phases that have different risks. Due to higher costs and access limitations associated with higher risk data, it may be preferable to complete any processing that involves higher risk data/data points as soon as possible in the research process, and continue work with a lower risk dataset. Examples of what this might look like in practice:
- Dropping any variables that are not necessary for the research being done
- Replacing physical addresses with aggregate information, such as project specific identifiers or geographical regions
- Replacing actual dates/times with days since prior visit, or changing birthdate to age
- Creating unique IDs that are unaffiliated with any personal information to replace any identifiable ID information
- Aggregating demographic information so individual cases are less unique, such as age brackets instead of age, or combining smaller categories
Variables necessary for the research should be retained in the needed format. In some cases, this will mean that the risk of the data does not change after processing, and the rules associated with higher risk data will still apply. At all times, any applicable regulations and/or contractual obligations should be followed.
There are some instances where data risk may increase during data processing – this is most often due to the addition of information that was not in the original dataset. For example, merging or appending two or more datasets may result in higher risk dataset due to the resulting combination of information. The risk of the data you are working with should be assessed at each stage for appropriate storage and security.
Best Practices for Maintaining Research Data
- Always retain the original data for as long as legally or contractually required. If no clear timeframe or legal or other contractual requirement exists, a good rule of thumb is retaining the data 7 years past the end of the project.
- Use the data with the lowest possible risk for active research.
- High risk data should only be accessed from UNL managed devices that have been formatted for such use, and only using UNL storage systems appropriate for the data. ITS can assist with device and storage settings.
- Data access should be limited to only approved persons, following regulatory and contractual guidance. For example, this may mean adding collaborators to an approval form, making sure others have read and signed a data access agreement, or working with Sponsored Programs to create a data use agreement.
Applicable NU Policies: Executive Memorandums 16, 41, and 42
The University of Nebraska is committed to the safeguarding of research data in accordance with all applicable federal, state, and University regulations. Those involved in research activities at the University of Nebraska have certain rights and responsibilities with respect to research data. All data from sponsored or non-sponsored research activities must be recorded, maintained, and made accessible in a reasonable and responsible manner by research personnel and in accordance with all applicable federal, state, and University requirements.
Research Records Best Practices
This guidance discusses the best practices for investigators to ensure quality research records and data integrity, in both paper and electronic formats.
UNL Guidance on research records best practices:
Sensitive, Restricted, or Confidential Data & Issues to Consider
Research data, or data that becomes part of the research record, can vary greatly depending on the research area and discipline involved. In general, the following are some different types of data that research personnel should be particularly cognizant of:
- Private health information (PHI, regulated by HIPAA): Sensitive patient health data can include insurance-related data, actual medical information, and personal data about patients, such as social security numbers, addresses, and other sensitive information, which should not be publicly available.
- Private individual information (PII): Such data includes social security numbers, addresses and phone numbers, and other personally-identifiable data that could potentially be used for identity theft and other illicit activity.
For PHI or PII, the IRB application process requires research personnel to address issues related to subject privacy and confidentiality (HIPAA, FERPA, EU GDPR etc). The following is important to keep in mind when seeking IRB approval:- Collect only the minimum necessary subject identifiers. PIs must be able to provide justification as to why they need to maintain or store this information.
- In the IRB application, PIs must address the method of collecting, recording, coding, maintaining, and storing data. In addition, PIs must specify who will have access to the data and at what point subject identifiable data will be de-identified or destroyed.
- Remove/destroy subject identifiers as soon as they are no longer needed.
- Limit physical access to any area or computer that contains subject identifiers.
- Limit electronic access to any computer that contains subject identifiers and follow the data security levels as applicable to your protocol (Low, Medium, High Levels).
- Avoid storing subject identifiable data on portable devices (such as laptop computers, digital cameras, portable hard drives including flash drives, USB memory sticks, iPads or similar storage devices) as these devices are particularly susceptible to loss or theft. If there is a necessity to use portable devices for initial collection of subject identifiers, the data files must be encrypted, and subject identifiers transferred to a secure system as soon as possible.
- Remove necessary subject identifiers from data files, and encrypt data files if stored electronically. Identifiers should be stored in a physically separate and secure location from the data files, and associated with the data files through a key code that is also stored in a separate and secure location.
- If subject identifiers will be retained in the data files because of the specific needs of the research study, additional justification must be provided by the Investigator to justify retention. Again, if the data are stored electronically the files must be encrypted.
- Use only secure modes of transmission of data; subject identifiers submitted over a public network must be encrypted.
- In the informed consent document, PIs must describe the extent, if any, to which confidentiality of records identifying subjects will be maintained.
- Be cognizant of the possibility of meta-data and inadvertent access to identifiers.
- If there is a breach of confidentiality of the research data which causes harm or places subjects or others at a greater risk of harm (including physical, psychological, economic, or social harm), the PI must report this information to the IRB in accordance with HRPP policies.
- Collecting IP addresses: If the research team plans to use electronic surveys, such as Qualtrics, or other electronic means of collecting data, PIs must plan for and address whether or not IP addresses will be collected or accessible which would allow for the identification of research participants. The UNL IRB and some international standards consider IP addresses to be identifiable information.
- Some PIs wish to collect the IP addresses of survey participants to provide a method of determining whether the user has previously completed the survey. In contrast, some PIs have no use for IP addresses but may not recognize that the survey software they are using is collecting this information. This is important to consider when conducting surveys, especially if the consent process indicates that a participant’s responses will be anonymous. When using Qualtrics, or other online survey software, unless this information is necessary to collect, PIs should check the option to anonymize the data collection process and not collect IP addresses. If IP addresses are necessary to the research, PIs must include in the consent process that they will be recording this information.
- Reidentification of “Anonymized Data”: Researchers typically employ a number of techniques in order to de-identify or anonymize research data. However, in some cases these techniques may not be enough in order to safeguard the identifiability of human research participants. In these instances, when research results are published, shared, or released, if appropriate measures are not in place, re-dentification could occur. Re-identification occurs when identifiable information is discoverable in scrubbed or so-called “anonymized” data. When a data set is re-identified, either direct or indirect identifiers become known and the individual can be identified. Direct identifiers reveal the identity of the person involved, while the indirect identifiers will often provide more information about the person’s preferences and habits. Re-identification generally can occur through three methods:
- Insufficient de-identification: Re-identification can occur when in-direct identifiers are left in a data set, whether unintentional or not. Researchers must also be particularly cognizant of the size and type of subject population(s) involved in their research.
- For example, a data set could potentially be released that has name, birth date, and addresses removed. However, a significant enough number of other identifiers could inadvertently still remain in the data set, such as zip codes, IP addresses, and gender, that would potentially allow for re-identification.
- Or another example might be a publication could reference information regarding a very small and specific subject population. Along with the publication noting that the PIs are from UNL or a Midwestern University, it may be rather easy for re-identification to occur because of the very specific population, time frame of data collection, or specific research topic.
- Pseudonym reversal: Some pseudonyms are designed to be reversible and a “key” is kept to reverse the process, however, this still places the security of the data at risk. Second, the longer the same pseudonym is used for a specific individual, the easier it may be to re-identify that individual. Finally, if the method used to assign pseudonyms is discovered or inadvertently released, it is possible that participants could be identified.
- Combining or Linking datasets: When two or more anonymized datasets are linked together, it may be possible for them to be used to unlock other anonymized datasets. Once one piece of data is linked to a person’s real identity, that data can then potentially be used to unlock the anonymity of any identity associated with the data. The ability to link even supposedly innocuous data exposes people to potential harm due to re-identification. It is important to note that once data is released publicly, its protection can no longer be strengthened, it can only be weakened. Ensuring appropriate and proactive de-identification practices and procedures are in place at the onset of the research will help avoid unwanted breaches of this nature.
- For example, in 2006, Netflix publicly released one-hundred million records revealing hundreds of thousands of user ratings from 1999 through 2005 and offered a million-dollar prize for the first team to significantly improve Netflix’s movie recommendation algorithm. Although the data contained no direct identifiers, within weeks of the data’s release, two researchers were able to re-identify a subset of specific people by cross-referencing the Netflix data with IMDB.com ratings.
- Additional Resource: The National Institute of Standards and Technology’s (NIST) paper on De-Identification of Personal Information
- Insufficient de-identification: Re-identification can occur when in-direct identifiers are left in a data set, whether unintentional or not. Researchers must also be particularly cognizant of the size and type of subject population(s) involved in their research.
- Restricted Data Sets: Restricted data is defined as data that cannot be released directly to the public research community due to possible risk(s) to study participants and the confidentiality promised to them. Gaining access to these datasets require appropriate approvals, security, and processes to be in place; researchers who wish to use these files must understand the requirements and responsibilities involved in gaining access. PIs should be aware that funds for data purchase or data security plans may also need to be included in the proposal budget. A number of restricted data sets are available and gaining access to them, along with the security and processes required, can differ among the controllers of licensing the data sets. In addition, genomic data sharing information is also available but subject to similar controls. PIs must understand the importance of having a process in place regarding agreements and IRB approval (if applicable) prior to requesting or creating these type of data sets. The following are two common examples:
- When the Institute of Education Sciences (IES) through its National Center for Educational Statistics (NCES) conducts surveys, the data collected sometimes includes individually identifiable information or confidential/sensitive information which is protected by law. The various data sets available can be found here. NCES/IES Restricted-Use data Licenses impose significant restrictions on who can have a License, who can access the data, and where and how the data can be housed.
- Researchers must be aware that substantial preparation is key to being approved for a new NCES/IES Restricted-Use data License. It is important to note that all information security requirements must be in place before NCES/IES will consider granting a researcher a NCES/IES Restricted-Use data License. A few examples of NCES/IES restrictions to consider:
- NCES/IES Restricted-Use data can only be stored and used on a stand-alone, non-networked, password-protected, desktop computer.
- The stand-alone desktop computer must be housed in a locked, secure room. Please be aware that this secure data space would need to be suggested by the researcher and reviewed/approved as feasible by the IRB and NU ITS.
- Access to the secure data room and data is limited to those who have submitted a signed, notarized affidavit of nondisclosure.
- Only certain individuals with signed affidavits are allowed access to the data on a single NCES/IES Restricted-Use data license.
- Researchers must be aware that substantial preparation is key to being approved for a new NCES/IES Restricted-Use data License. It is important to note that all information security requirements must be in place before NCES/IES will consider granting a researcher a NCES/IES Restricted-Use data License. A few examples of NCES/IES restrictions to consider:
- Researchers can request access to data sets from the Centers of Medicare and Medicaid (CMS). CMS offers researchers and other health care professionals a broad range of quantitative information, from estimates of future Medicare and Medicaid spending to enrollment, spending, and claims data, and a broad range of consumer research to help its partners and staff. CMS also conducts demonstration projects to explore alternative policies of health care coverage and delivery. These demonstration projects typically cover a limited timeframe, geographic area, and scope of coverage. In many cases, however, researchers must be careful to note that CMS may have or provide data sets that contain sensitive/restricted information, such as PHI/HIPAA controlled data that requires careful consideration and clear security parameters.
In many cases, such as the examples above, a data security plan and institutional (UNL) signature/approval is required in order to receive and safeguard this data.
- When the Institute of Education Sciences (IES) through its National Center for Educational Statistics (NCES) conducts surveys, the data collected sometimes includes individually identifiable information or confidential/sensitive information which is protected by law. The various data sets available can be found here. NCES/IES Restricted-Use data Licenses impose significant restrictions on who can have a License, who can access the data, and where and how the data can be housed.
- Military and government data: Data specific to government programs or under specific contract terms regarding the governance of the data, particularly those related to research that could have a military or dual-use (civil or military application) and operations is carefully regulated.
- When addressing the need for security with data that has export control requirements, it is important for research personnel to recognize that a case-by-case approach will likely be necessary when receiving or creating controlled data.
- PIs must understand and adhere to contract requirements, particularly clauses that restrict foreign national access, specific IT security requirements, or publication restrictions:
- Publication is not allowed by the sponsor due to the security level of the research data -or-
- Publication is allowed, however a certain period of time for review and approval is required. This time frame can vary, but typically contracts stipulate 30-45 days for the PI to submit to the sponsor information planned for publication, and for the sponsor to provide approval or redaction in order for the publication to move forward.
Tele/Video Conferencing (Zoom/Microsoft Teams)
Research personnel must be aware of security concerns or issues that can arise when utilizing tele/video conferencing technology. University licensed technology (Zoom/Teams) must be used when discussing research business, conducting interviews with participants, and/or other types of research related meetings. For security and confidentiality, the following are some precautions to consider:
- Enable wait for host to join so that the meeting cannot start without the host/responsible leader.
- Enable/disable a participant or all participants if recording a video session.
- Use of passwords to enter a virtual meeting space should be used at all times.
- Use of the screen-sharing feature should be used with caution (whether it is from researchers to participant(s)/to other personnel or vice versa.
- Participant instructions on how to maintain confidentiality and privacy standards should be described as part of the IRB and Export Control review process. These instructions could include instructions to close all other programs, windows, software, browser tabs, etc. during the research-related call.
- Be aware that the chat feature provides a transcript of all chats occurring throughout the meeting to the host at the end of the session. Be professional and courteous when using the chat feature and be cognizant of what information is being shared via chat and whether or not it is restricted, sensitive, or confidential.
- When using the record feature in Zoom, you may need to save a copy of the recording to your local UNL desktop hardware to then upload it to a UNL secure storage location, or you may utilize Zoom’s Cloud Recording option, provided that you 1) utilize the passcode protection and/or the “available only to viewers logged in to the account” features and 2) if you are working with export controlled research, you must verify whether recording/upload/cloud features can be utilized or not.
- Saving to Zoom’s Cloud does allow the ability to store in-meeting chat messages, shared files, and automatic transcription services, which are stored encrypted as well.
- As part of NU ITS processes, two-factor authentication (2FA) should already be enabled on your account in order to provide an extra line of defense against malicious attempts to access data.
- Most importantly, be cognizant of what is being discussed and/or shared virtually. If the research requires medium to high levels of security, research personnel must understand what may or may not be discussed/shared. Sticking to general, publicly available information and topics is always preferred.
Please be sure to review Zoom’s whitepaper (as well as their Encryption Whitepaper) describing certain features of the technology.
Travel & Data Security
This guidance is intended to help inform travelers on University related research business, with university owned equipment regarding security responsibilities and best practices for protection of physical and electronic research data. Research personnel are required to fully understand the risks associated with working with University research data when off campus and should seek the assistance from Research Compliance, Integrity, and Security and NUITS staff to help evaluate the appropriate level of security for their travel needs. The following are some best practices that should be followed when traveling.
Remember, the best way to protect research data is to not travel with it unless absolutely necessary. Do not travel with any devices or data you cannot replace, would not want to lose, or that could pose a breach of personal, identifiable, confidential, restricted, sensitive, or proprietary information.
- In many foreign countries you often cannot have the same level or expectation of privacy. Assume the possibility that any and all communications you work on are insecure.
- If traveling on university related business, ensure that you are completing or reading Export Control travel checklist notifications along with following University travel policies. These notifications along with your travel plans submitted via Concur are designed to help you know if there are any travel restrictions, concerns, or export controls that might affect you so that you can plan accordingly.
- Where possible, limit the number of IT devices including cell phones you take with you on your trip.
- Limit the amount of research data you take with you, to only what is absolutely required for the trip. Ensure you make appropriate backups and have implemented appropriate security protections (such as de-identifying sensitive or identifiable data, or using encryption) prior to the trip. Be prepared for the possibility that your data may be exposed or taken during the course of your travel.
- In general, you should not be accessing or traveling with Medium and High Risk research data. If you plan to access and work with Medium or High Risk research data in the country you visit, have your departmental support person and Research Compliance, Integrity, and Security staff assist to ensure you have permission or appropriate licensure to handle or access the data from the country you will be visiting. (e.g. some countries can limit or restrict use of VPN).
- Keep in mind that some software, particularly encryption, is export controlled. Discuss your options with Export Control staff and NUITS before leaving. In most foreign countries, using the operating systems’ built-in encryption is not problematic.
- Be aware that current export control laws give Customs and Border Patrol the authority to enact an onsite inspection on ANY device you may be carrying. This includes cell phones, laptops, tablets, and other computing devices. These organizations may even demand your passwords, PINs, and/or encryption keys and have authority to detain you if you do not comply. If a device is identified as having probable investigative cause it could be confiscated for analysis, running the risk of exposing sensitive information, and possible permanent loss of the device.
- When traveling internationally, be aware of the different voltage requirements. Investigate and purchase a plug adapter to accommodate the type of electrical outlets used at your destination. Power fluctuations in some travel destinations can cause serious damage to university equipment, so look into whether you may need a surge protector if there is a risk of danger.
- Review the US Department of State Traveler’s Checklist at http://travel.state.gov/content/passports/en/go/checklist.html including the detailed country information search tool at the bottom.
- Consider checking out a wiped laptop from NU ITS or UNL Export Control in order to ensure no data is inadvertently shared.
- Additional considerations:
- Do not set your web browser to remember login passwords. Always clear out the browser cache before you leave. (Check your Internet Options, and delete any saved files, pages, passwords, or the entire browser history.)
- Make sure your Antivirus software and all of your operating system and program updates are current.
- Do not store sensitive personally identifiable information (PII), private health information (PHI), or other restricted (Medium/High risk) data on your device. Should the device fall into the wrong hands the sensitive data or software could become compromised.
- Consider installing the UNL VPN client software and use it to secure your connection to university resources.
- Unsecured wireless can easily be intercepted so whenever possible, use secured wireless services with a password, or similar.
- Ensure your computer is configured to automatically lock after a short period of inactivity, and require your password to resume (unlock) it. Never leave your computer turned on and logged in, even in your hotel room.
- To help track/locate stolen or lost personal devices, consider having ITS activate location software included on your device, or purchasing and installing location hardware and software products.
- Consider having IT set up your device(s) to allow you to remotely wipe the device in the event it is either lost or stolen.
- Whenever possible, DO NOT accept flash drives or other computer hardware offered from a non-University of Nebraska source. This can often be a tactic used to access your computer files or place a virus into your devices. If you do accept it, DO NOT use it or connect it to your computer or other devices, turn it in instead to your RCIS or IT staff upon your return.
- Considering buying some form of physical locking device – a laptop security cable or similarly appropriate technology.
While you are traveling:
- If working with protected information in a public place e.g.. at a conference, be aware of your physical location as shoulder surfers (persons observing what you may be working on) are a risk.
- Disable infrared and or Bluetooth ports and any other device communication features when they are not in use.
- Do not leave your mobile device unattended in your hotel room, or at any time. If you are not using it, lock it away in your hotel safe, or if you do not have one, lock it away in your luggage. In some international destinations, laptops are a sign of wealth and could attract the attention of thieves. Limit the use of your devices in public, where possible.
- NEVER access research data from a public computer or collaborator’s device while traveling.
- Before you return, be sure to transfer all data files that you handled while traveling back to your personal or departmental file storage location and then delete the files from your portable device. It may be a good idea to create a list of equipment before you leave and check it to make sure you’re not leaving anything behind.
Returning from traveling:
- Check to ensure all removable media and documents you may have used on your trip are appropriately stored or destroyed.
- It is a recommended best practice to change your NU passwords upon your arrival back to campus. This is just in case someone was able to somehow obtain it while you were traveling.
- If you traveled abroad, consider having ITS reformat/reinstall portable devices that were used outside of the US before connecting to either your home or the campus network. (For US travel, also consider having your portable device reformatted/reinstalled if you suspect an issue.) This is to ensure the device is free of malicious software, keystroke loggers, remote access trojans, or other problems that can be introduced in the course of your travel.
- If you happened to encounter any strange conversations or occurrences regarding your travel or research data security, have a conversation about this with RCIS or IT staff. Turn in any devices that you may have received as gifts and do not use them.
Additional Resources
- Board of Regents Policies and Bylaws
- Data Management Planning Tool
- Step-by-Step Guide for Redacting in Adobe Acrobat Pro DC
- NIH, Access to Research Data (2.3.11.2.3) & Protecting Sensitive Data and Information Used in Research (2.3.12)
- NSF Research Security webpage
- NU ITS Safe Computing Guidelines
- NU ITS SSN & PII Best Practices
- HRPP Policies and Procedures
- ECCP Policies and Procedures
- ECCP Guidance regarding CUI/CDI/Microsoft 365 US Government






